Top Insights
Security
Reverse Email Lookup: 9 Best Tools to Find Emails Reversely
Now is the time for you to get to business! There are many online reverse email lookup services. While some websites provide more...
ByAlbert LukmanovNovember 22, 202510 Best Cloud Security Tools to Keep Your Data Safe
Have you tried any cloud security tools? These tools are specifically to protect your cloud environment. Cloud computing platforms are becoming more popular...
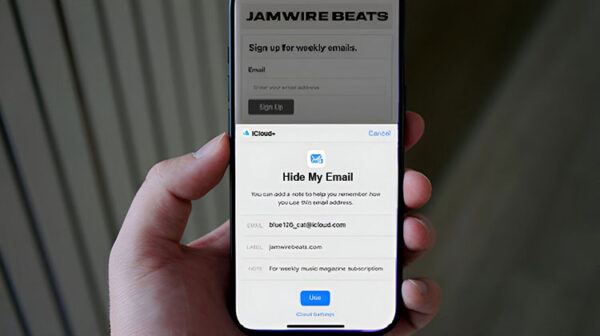
ByAlex NevolinOctober 31, 2025What Is Hide My Email? How It Works on iOS and iCloud
For the iOS 15 feature, which is designed to be extremely easy to use, Hide My Email comes with a lot of features....
ByMary IschenkoOctober 28, 2025Top 6 Free IP Stressers to Test Your Network Security
In the current digital world, security, network administrators, professionals, and gamers frequently require testing the strength of their networks and servers. This is...
ByAlbert LukmanovOctober 13, 2025Best VPN for Steam: Reduce Lag & Bypass Restrictions
A VPN for Steam can provide many advantages. Whether that means playing on regional servers when abroad, accessing normal regions when at home,...
ByDenis BitsonOctober 9, 20257 Fast and Reliable Proxies for School Networks
Internet access is treated by school networks as if it’s a national security concern. I spent 20 hours searching best proxies for school...
ByAlex NevolinOctober 4, 2025Are Cracked VPNs Safe? 5 Alternatives for Secure Browsing
Are you looking for a cracked VPN? Relax for a few minutes and consider the dangers. I’m aware that premium VPNs are expensive,...
ByAlbert LukmanovSeptember 28, 2025How to Block Websites on iPhone in 5 Simple Methods
Are you concerned that your child is accessing inappropriate online material via their iPhone? Are certain websites becoming distracting at work, and you...
ByMary IschenkoSeptember 27, 2025How to Find Network Security Key on Windows 10
What is a security key? What kinds of network security keys are available? What is the best way to find the network security...
ByAlex NevolinSeptember 20, 2025What Is a Residential Proxy? Complete Beginner’s Guide (2025)
There have likely been instances where you needed to appear as if you were in another region and but not actually being in...
ByAlbert LukmanovAugust 26, 2025